The Session Initiation Protocol (SIP) is the unsung hero of modern internet communication. It's essentially the signaling language that powers real-time conversations online—everything from voice and video calls to instant messaging. Think of it as the foundational technology that makes Voice over Internet Protocol (VoIP) and cloud telephony work.
The Engine Behind Digital Conversations

I like to think of SIP as the air traffic controller for your digital conversations. Just like a controller coordinates take-offs, flight paths, and landings, SIP is responsible for starting, managing, and ending every call or video conference. It doesn't carry the actual audio or video—other protocols handle that—but it meticulously sets up the "flight path" for that data to travel between you and the person you're talking to.
This protocol was a game-changer, designed to replace the rigid and expensive infrastructure of old-school phone lines. By moving communications onto IP networks, SIP cut the cord, freeing businesses to connect with anyone, anywhere, as long as they have an internet connection.
What Does SIP Actually Do?
When you break it down, SIP has a handful of core responsibilities that work in concert to create a smooth communication experience. It's these duties that make internet-based calls possible.
- User Location: It has to find the person you're trying to call on the network, figuring out their current IP address.
- Session Setup: This is the "INVITE" stage, where it sends a request to the other party to start the call.
- Media Negotiation: Both sides need to agree on the technical details, like which audio codecs or video resolutions to use. SIP handles this handshake.
- Session Management: Need to put someone on hold, transfer a call, or add a person to a conference? That's SIP managing the session in real-time.
- Session Teardown: When the conversation is over, SIP makes sure the session is closed out cleanly.
This move to IP-based communication has sparked incredible growth. In fact, the SIP trunking market in the Middle East and Africa alone is expected to hit around USD 1,551.30 million by 2029. Businesses are jumping on board because the efficiency gains are just too big to ignore.
At its heart, SIP is a surprisingly simple, text-based protocol that orchestrates incredibly complex multimedia sessions. Its primary job is to make sure two or more people can find each other on a network and agree on how they're going to talk.
To get a clearer picture, let's look at SIP's main jobs using that air traffic controller analogy.
SIP's Core Functions at a Glance
The following table breaks down the primary roles of the SIP protocol in managing a communication session, from start to finish.
| Function | Description | Analogy (Air Traffic Controller) |
|---|---|---|
| Session Initiation | Establishes the connection and call parameters between participants. | Clearing the flight plan and giving the 'go' for take-off. |
| Session Management | Modifies the session, handling transfers, holds, or adding participants. | Rerouting a flight mid-air or changing its destination. |
| Session Termination | Ensures the connection is properly closed when the call ends. | Guiding the plane to a safe landing and arrival at the gate. |
Understanding these functions is key to grasping how modern telephony operates without relying on traditional phone networks. SIP is the invisible framework holding it all together.
How a SIP System Actually Works

To really get what the SIP communication protocol does, you need to meet the key players that make up a SIP network. The protocol itself is just a rulebook, but its real power is in how these different components talk to each other to get calls where they need to go.
Think of it like a digital postal service, with an incredibly organized system to make sure your messages—whether a voice call or video chat—find their way every single time.
At the edge of this system are the devices we all use to communicate. In SIP terminology, these are called User Agents.
The Senders and Receivers: User Agents
A User Agent (UA) is any endpoint that can kick off or answer a SIP session. This could be a physical IP phone on your desk, a softphone app running on your laptop, or the calling feature in a mobile app. In our postal service analogy, the User Agents are both the person writing the letter (the caller) and the person it's addressed to (the callee).
Every User Agent wears two hats, depending on the situation:
- User Agent Client (UAC): This is the part of your device that starts the conversation. When you dial a number or click a "call" button, your device's UAC fires off a SIP request. It's the equivalent of dropping a letter into the mailbox.
- User Agent Server (UAS): This is the component that's always listening for incoming calls. When someone calls you, it's your UAS that receives the SIP request and has to decide what to do—accept, reject, or maybe even redirect the call.
So, every SIP-enabled device is both a client and a server, switching roles based on whether it’s making or taking a call. But these devices don't just shout into the void of the internet hoping to find each other. They rely on specialized servers to manage all that traffic.
The Central Post Office: SIP Proxy Server
While User Agents could technically connect directly, it would be chaotic and inefficient at any real scale. That's why most SIP traffic flows through a central hub known as a Proxy Server. This server is the main post office in our analogy. It's where all the requests are received, sorted, and sent on their way.
When your UAC wants to make a call, it sends the request to a Proxy Server, not directly to the person you're calling. The proxy then acts as an intelligent middleman. It might handle things like authentication (making sure you’re allowed to make the call), applying routing rules, or even forking a request to multiple devices at once—like making your desk phone and mobile app ring simultaneously.
A Proxy Server is the intelligent traffic director of a SIP network. It doesn't just forward messages; it makes routing decisions, enforces policies, and ensures that call requests are handled efficiently and securely before they reach the intended recipient.
The Master Address Book: Registrar Server
So, how does the Proxy Server know where to send the call? It checks with the Registrar Server. Think of the Registrar as the master address book for the entire network.
When a User Agent, like your softphone, comes online and connects to the network, it sends a REGISTER message to the Registrar. This message basically says, "Hello, I am User 'Alice,' and for the time being, you can find me at this specific IP address."
The Registrar stores this location information, creating a map between a user's permanent SIP address (like al***@*****ny.com) and their current, temporary IP address. When a call comes in for Alice, the Proxy Server asks the Registrar for her current location and forwards the call there. This is what lets you receive calls on any device, anywhere, as long as it's signed into the network. Given that SIP communication often operates within complex environments, understanding the fundamental concepts of distributed systems can be beneficial.
The Helpful Forwarding Service: Redirect Server
Finally, there's the Redirect Server. This one works a bit differently from a Proxy. A Redirect Server doesn't forward the call request on behalf of the caller. Instead, it looks up the recipient's location and tells the original caller where to find them.
It’s like a postal forwarding service. If you send a letter to an old address, the post office doesn't re-route it for you; it sends you a note back with the new, correct address and says, "Try sending it here instead." The caller's device (the UAC) then has to send a brand-new request directly to that updated location. While less common than a Proxy, this approach is useful in certain network designs.
Following a Standard SIP Call Flow
To really get a feel for how SIP works in the real world, let's trace the journey of a single phone call from start to finish. This play-by-play will show you how all the different User Agents and servers we've discussed coordinate to make a call happen. It’s less abstract when you see it in action.
Think of the whole process as a digital conversation between devices. Every message has a specific job, building on the one before it to create a reliable and orderly way to manage the call.
Kicking Off the Conversation: The INVITE Request
It all starts when one person—we’ll call her Fatima—wants to call her colleague, Ahmed. When Fatima picks up her IP phone and dials, her device (the User Agent Client) springs into action and creates a special message.
This first message is called an INVITE request. It’s basically the digital equivalent of knocking on a door and asking, "Can Ahmed come out and talk?" This INVITE is packed with important info, like Fatima’s SIP address, Ahmed’s SIP address, and the technical specifics of the call, such as which audio codecs her phone supports.
But Fatima's phone doesn't send this message straight to Ahmed. Instead, it fires it off to its local SIP Proxy Server, which acts as the call's traffic cop.
Finding the Recipient and Responding
Once the Proxy Server gets the INVITE, its first job is to figure out where Ahmed is. It pings the Registrar Server—the network's address book—to look up Ahmed's current IP address. The Registrar replies with the last known location of Ahmed's device.
With Ahmed’s location in hand, the Proxy forwards the INVITE request over to his device (the User Agent Server). Ahmed's phone receives the INVITE and, just as you'd expect, starts ringing.
To let Fatima know that the call is going through, Ahmed’s phone immediately sends back a preliminary response—usually a 180 Ringing message. This message travels back through the Proxy to Fatima's phone, which cues the familiar ringing sound in her earpiece.
This digital handshake is crucial. It ensures the caller isn't just sitting in silence, wondering if anything is happening. The 180 Ringing message confirms the invitation was delivered and is just waiting for an answer, which prevents frustrating call timeouts.
Making the Connection: The OK and ACK Handshake
When Ahmed finally answers the call, his device sends the most important response yet: 200 OK. This message is the green light, signaling that he's accepted the call. It travels back through the Proxy to Fatima’s phone, letting it know the connection is a go.
The 200 OK message also includes Ahmed's own media settings, confirming which audio codec they'll both use for the conversation. This ensures both phones are speaking the same technical language from the get-go.
This diagram shows the core three-way handshake that locks in a successful SIP connection.
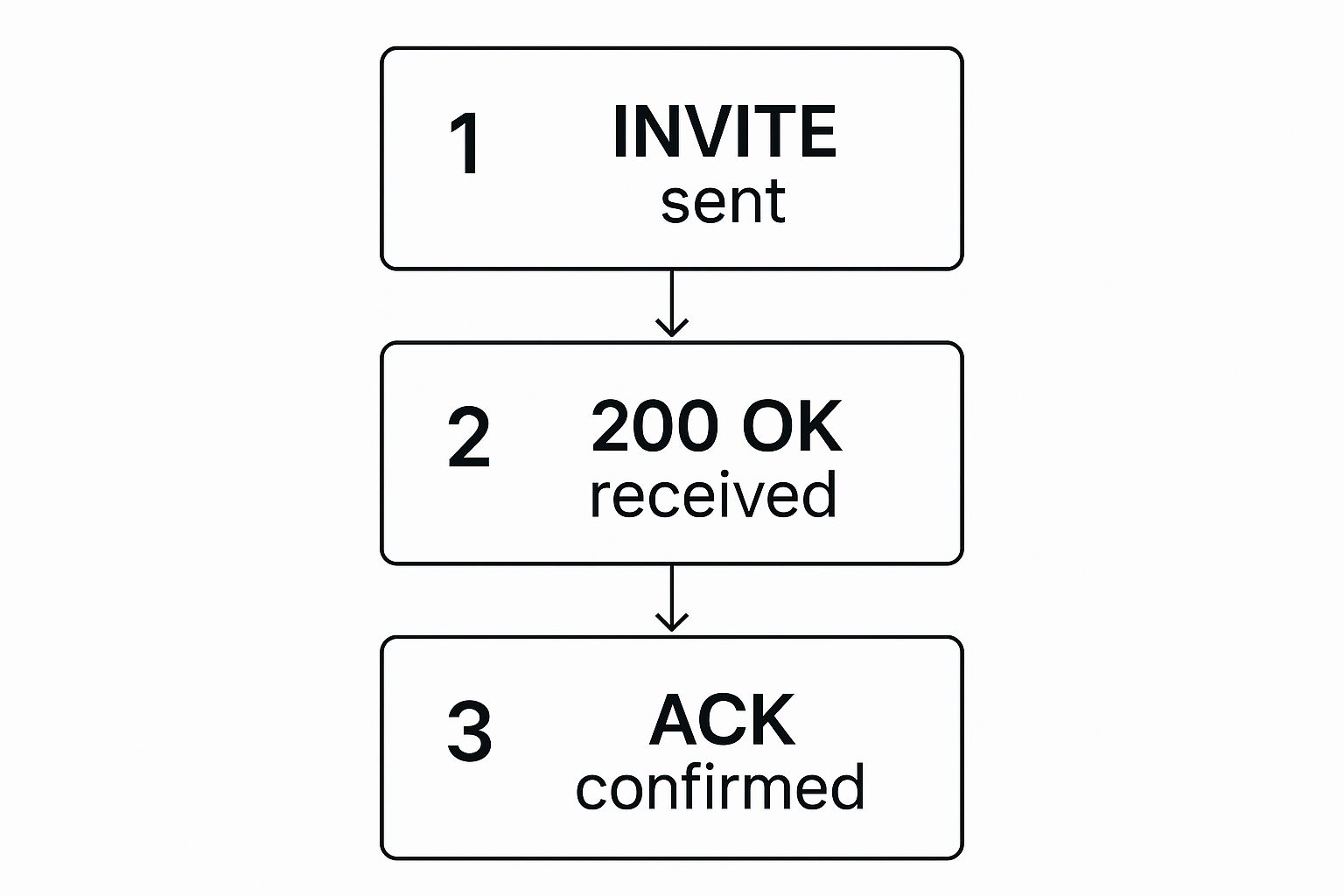
This simple flow—INVITE, OK, ACK—confirms that the invitation was sent, accepted, and acknowledged, creating a solid foundation for the actual conversation.
To seal the deal, Fatima's phone sends one last message: an ACK (Acknowledge). This tells Ahmed's phone, "Got your OK, loud and clear." With the ACK sent and received, the setup is complete. Now, the actual voice data can start flowing directly between Fatima and Ahmed.
Gracefully Ending the Session
Once the call is connected, SIP takes a back seat. The actual audio is exchanged directly between the two phones using a different protocol, usually RTP (Real-time Transport Protocol). SIP only steps back in when someone is ready to hang up.
Let's say Fatima ends the call first. Her phone sends a BYE request to Ahmed's phone. His device then replies with a final 200 OK to confirm it received the BYE, and the session is officially over. All the network resources are freed up, and the call is logged as complete. This clean teardown is a hallmark of SIP, ensuring no connections are left dangling.
Securing Your SIP Communications

As more and more businesses lean on the SIP communication protocol for their day-to-day operations, protecting those conversations is no longer just an IT concern—it’s a business imperative. Moving your communications over the internet gives you incredible flexibility, but it also opens the door to security threats that simply weren't a factor with old-school phone lines.
These aren't just abstract risks; they carry real-world consequences for your business. We're talking about everything from someone eavesdropping on a sensitive financial call to toll fraud, where attackers hijack your system to make expensive international calls and leave you holding the bag. Getting a handle on these vulnerabilities is the first step toward building a truly resilient communications setup.
Common Threats to Your SIP Network
Attackers have VoIP systems squarely in their sights, often seeing them as a soft target for financial gain or a stepping stone into your wider corporate network. Knowing what you're up against is half the battle.
- Eavesdropping: Without the right encryption, your call data travels in the clear. A bad actor could easily intercept these data packets and listen in on private company meetings or confidential client calls.
- Toll Fraud: This is one of the most financially crippling attacks out there. Hackers find a way into your phone system and use it to dial premium-rate numbers, racking up enormous charges that you are responsible for.
- Denial-of-Service (DoS) Attacks: Imagine your phone lines going completely dead. A DoS attack does just that by flooding your SIP servers with junk traffic, overwhelming the system and blocking any legitimate calls from getting through. It can grind your entire business, from sales to support, to a halt.
- Registration Hijacking: If an attacker gets their hands on a user's login credentials, they can register their own device as that user. This lets them make and receive calls on your company's dime and, even worse, intercept critical communications.
Defending against this stuff isn't about a single magic bullet. It requires a layered strategy that protects both the signaling messages that set up the calls and the media streams that carry the actual audio or video.
Your First Line of Defense: Encryption Protocols
The good news is that the SIP standard was built with security in mind. Two protocols, in particular, are your best friends here: TLS and SRTP. They work in tandem to create a secure bubble around your calls.
Think of it this way: TLS is like putting the envelope (the call setup info) into a locked, tamper-proof bag before sending it. Then, SRTP ensures the letter inside (your voice or video) is written in a secret code that only the intended recipient can decipher.
First up is Transport Layer Security (TLS), which encrypts the SIP signaling messages. These are the INVITE, OK, and BYE messages that kick off, manage, and end a call. By scrambling this setup data, TLS stops attackers from seeing who is calling whom or messing with the call session itself. For a closer look at this foundational layer, you can explore the specifics of SIP over TLS in our detailed guide.
Next, we have the Secure Real-time Transport Protocol (SRTP). This protocol's job is to encrypt the media stream—the actual voice and video content of your conversation. With SRTP in place, even if an attacker manages to intercept the data packets, all they'll get is unintelligible gibberish without the correct decryption key.
The Network Guardian: Session Border Controllers
While encryption is non-negotiable, a complete security strategy also needs a dedicated gatekeeper. That's where a Session Border Controller (SBC) comes in. An SBC sits at the edge of your network, acting as a smart, powerful security guard for all your SIP traffic.
It inspects every packet coming in and going out, enforces your security rules, and effectively hides your internal network layout from the outside world. A well-configured SBC can spot and shut down suspicious activity—like the kind you'd see in a DoS attack or a toll fraud attempt—long before it ever threatens your core communication servers. It's an essential piece of the puzzle for any organization that's serious about locking down its SIP communications.
Why SIP Is Essential for Modern Business
Getting a handle on the technical side of the SIP communication protocol is a great start, but its true value really clicks when you see how it fuels business growth and streamlines operations. For any modern company, especially in a fast-paced market like the UAE, SIP isn't just another piece of technology. It's the strategic backbone for flexible, affordable, and connected communications—the engine powering everything from cloud phone systems to advanced contact centers.
The first thing most businesses notice is the massive drop in their telecom bills. By swapping out old, rigid phone lines for versatile SIP trunking, you get to ditch expensive physical hardware and sky-high per-minute call rates. This simple move lets you run all your voice and data traffic over a single IP network, which not only saves a ton of money but also makes managing vendors a whole lot easier.
This shift away from legacy systems is picking up serious speed across the region. Here in the UAE, the move to SIP trunking is driven by major upgrades to our telecom infrastructure and the boom in cloud services. Over the last ten years, significant government investment in high-speed internet and data centers has created the perfect environment for IP-based protocols like SIP to thrive. This has kicked off a migration from the traditional Public Switched Telephone Network (PSTN) to IP telephony, as businesses look to cut costs and boost reliability. You can discover more insights about what SIP is in our complete guide on the topic.
Let's take a look at how SIP stacks up against the old way of doing things.
Traditional Phone Lines vs SIP Trunking
The table below breaks down the key advantages of adopting SIP-based communication over legacy telephone systems. It's a clear picture of why so many businesses are making the switch.
| Feature | Traditional Phone Lines (PSTN) | SIP Trunking |
|---|---|---|
| Cost Structure | High monthly line rental and per-minute call charges | Lower monthly fees, often with bundled minutes and free internal calls |
| Infrastructure | Requires physical copper wires and on-site PBX hardware | Runs over your existing internet connection; minimal hardware needed |
| Scalability | Slow and costly; requires physical installation of new lines | Instant and software-based; add or remove channels in minutes |
| Flexibility | Tied to a physical location; difficult to move or reconfigure | Location-independent; use your business number anywhere with internet |
| Integration | Limited integration with other business applications | Natively integrates with CRM, UC platforms, and cloud software |
| Reliability | Vulnerable to physical line damage; limited failover options | Highly reliable with easy call rerouting and redundancy options |
As you can see, SIP trunking isn't just a minor upgrade—it represents a fundamental improvement in how businesses manage their communications infrastructure, offering agility and efficiency that traditional systems can't match.
Unlocking Unprecedented Scalability and Flexibility
Beyond the immediate cost savings, SIP gives you a level of agility that traditional telephony just can't touch. Picture your business growing or needing to adapt to a seasonal rush. With old-school phone lines, adding more capacity was a painfully slow process involving technicians, appointments, and physical installations. With SIP, scaling up or down is as easy as changing a software setting, often done in just a few minutes.
This kind of flexibility lets businesses pivot on a dime without being chained to rigid, long-term contracts. It means a logistics company in Dubai can instantly add more lines to manage a holiday shipping surge, or a financial firm can set up a virtual local number in Abu Dhabi without needing a physical office there.
The Backbone of Unified Communications
Maybe the most important role SIP plays is as the central nervous system for Unified Communications (UC). It’s the technology that tears down the walls between different communication tools, blending them into one seamless platform.
SIP is the protocol that allows voice, video, instant messaging, and presence information to coexist and interact seamlessly. It is what enables an employee to start a chat on their laptop, elevate it to a voice call, and then add video and screen sharing with a single click—all within one application.
This tight integration makes everyday workflows smoother and boosts team productivity. Think about it: an agent in a modern contact center can handle a voice call, reply to a WhatsApp message, and update a customer's record in the CRM, all from a single screen. That's possible because SIP is busy managing all those different communication sessions in the background. To get a better feel for the practical benefits, it's worth exploring these real-world SIP communication use cases, which show just how versatile it is.
By serving as the universal translator between different apps and platforms, SIP makes it possible to build powerful, all-in-one solutions. This capability is absolutely essential for companies in sectors like healthcare, finance, and logistics that are focused on building smarter, more customer-focused operations. SIP is no longer just a way to make phone calls; it’s a cornerstone of modern business strategy.
Common Questions About SIP
As SIP becomes the go-to standard for business communications, a lot of questions pop up. It's completely natural. Let's tackle some of the most common ones we hear to clear up any confusion and give you a solid grasp of how it all works.
What Is the Difference Between SIP and VoIP?
This is easily the most frequent question, and it's a great one because it gets to the heart of the matter. The easiest way to think about it is that VoIP (Voice over Internet Protocol) is the general concept, while SIP is a specific method for achieving it.
Imagine VoIP as the idea of "driving a car." It's the broad activity of getting from point A to point B using a vehicle. SIP, on the other hand, is like the "rules of the road"—it's the traffic lights, the stop signs, and the signals that cars use to start a trip, navigate intersections, and arrive at their destination safely.
So, VoIP is the what (making calls over the internet), and SIP is the how—it’s the signaling protocol that lets devices set up, manage, and tear down those calls.
Does SIP Only Handle Voice Calls?
Not at all, and this is where SIP truly shines. The "Session" in Session Initiation Protocol is a clue; it can refer to any kind of real-time communication, not just voice.
This versatility is exactly why SIP is everywhere today. It's the technology that makes all of these possible:
- Video Conferencing: Setting up and controlling video calls with multiple people.
- Instant Messaging: Establishing the connection for a real-time text chat.
- Online Gaming: Helping players connect for an interactive session.
- Presence Information: Sharing a user's status, like "available," "busy," or "away."
Because SIP can juggle all these different media types, it has become the foundation for modern Unified Communications (UC) platforms that bring voice, video, and messaging together in one place.
What Is a SIP Trunk and Why Do Businesses Need It?
Think of a SIP trunk as the modern, digital version of the bundle of old-school phone lines that used to run into an office building. Instead of physical copper wires, a SIP trunk uses your existing internet connection to connect your company's phone system (like a PBX) to the outside world's telephone network.
Businesses are making the switch to SIP trunking for two huge reasons: cost savings and flexibility. You get to ditch expensive, dedicated phone line rentals and take advantage of much lower call rates. In fact, in the Middle East and Africa, voice communication drives over 70% of the revenue for SIP trunking services. The ability to instantly add more call capacity or grab a local phone number in a new city gives businesses an operational edge that just wasn't possible before. You can explore more data on this in the SIP trunking services market trends from Data Insights Market Research.
In short, a SIP trunk turns your internet connection into a bundle of virtual phone lines. It’s the essential bridge between your IP-based phone system and the traditional phone network, offering scalability that legacy systems just can't touch.
Is Implementing SIP Difficult?
The honest answer is: it depends. The complexity really hinges on your starting point and what you're trying to achieve.
For a small business signing up with a cloud-based phone provider, the setup is often incredibly simple. The provider handles all the complex technical work on their end, so you're up and running quickly.
For a larger company looking to connect SIP to an existing, on-premise PBX, the project is definitely more involved. It often means reconfiguring parts of the network and installing a Session Border Controller (SBC) to handle security and manage traffic. That said, the growth of managed SIP services has made the technology far more accessible for everyone, turning what was once a daunting IT project into a much more straightforward process.
At Cloud Move, we specialize in building and deploying powerful telephony and contact center solutions designed for your specific business needs. Whether you're a small team just starting out or a large enterprise with complex requirements, our experts are here to guide you through a smooth transition to a modern communications platform. Book your free demo with Cloud Move today and let us show you what's possible.




